AI PCs Are Quickly Becoming the Key to Achieving Security and Productivity Goals
By: Dell Technologies and Intel View more from Dell Technologies and Intel >>
Download this next:
MSP: How to step in & save your client from cyberattacks
By: TruGrid
Type: Case Study
As a managed service provider, you often inherit existing technology stacks. What do you do when you know a current remote desktop service isn’t providing your client the protection they think it does?
Download this case study to discover how a regional MSP used TruGrid to reduce the exposure of a global real estate firm to cyberattacks.
These are also closely related to: "AI PCs Are Quickly Becoming the Key to Achieving Security and Productivity Goals"
-
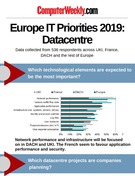
Infographic: 2019 Europe IT Priorities - Datacentre
By: TechTarget ComputerWeekly.com
Type: eGuide
In this infographic, we take a look at what technological elements of the datacentre are expected to be the most important in 2019, the most popular datacentre projects and which technologies and services are being deployed. Survey results taken from the 2019 IT Priorities survey carried out by ComputerWeekly.com, ComputerWeekly.de and LeMagIT.fr.
-
Computer Weekly 3 September 2019: From IT disaster to digital innovation at RBS
By: TechTarget ComputerWeekly.com
Type: Ezine
In this week’s Computer Weekly, we meet the man brought in to turn around the technology at RBS Group after its catastrophic IT outage. We examine the latest best practice in securing mobile devices in the enterprise. And we look at progress towards “passwordless” security.
Also featured:
- OpenShift is a key ingredient in the latest move in IBM’s long-running cloud strategy. We look at what it means.
- In the final part of our buyer’s guide to big data architecture, we look at how exponential growth in data is driving the IT industry to re-engineer long-held views of information management.
- Hyper-converged infrastructure (HCI) can be an easy win when it comes to datacentre infrastructure upgrades, but there are pitfalls. We look at how best to sidestep them.
Find more content like what you just read:
-
A Computer Weekly buyer's guide to zero-trust security
By: TechTarget ComputerWeekly.com
Type: eGuide
Zero trust is a conceptual architectural model that uses microperimeters and microsegmentation to secure corporate networks. In this 12-page buyer's guide, Computer Weekly looks at why trust should be considered a security risk and the need for additional authentication strategies to have an appropriate level of security.
-
Focus: IT Security in the Middle East
By: TechTarget ComputerWeekly.com
Type: eGuide
In this issue, we look at the challenges facing organisations in the Middle East as they increasingly rely on digital technologies to engage with customers and citizens.We also analyse specific risks to enterprises, such as malware sneaking into networks under the guise of encryption.
-
Computer Weekly - 2 March 2021: The most influential people in UK technology
By: TechTarget ComputerWeekly.com
Type: Ezine
In this week's Computer Weekly, we reveal our annual list of the 50 most influential people in UK IT, and talk to this year's winner, NHS Digital CEO Sarah Wilkinson, about an unprecedented year of challenges. Also, we examine the best software patching strategies and see how the pandemic has affected women in tech. Read the issue now.
-
A Computer Weekly Buyer's Guide: Office Productivity for Home Workers
By: TechTarget ComputerWeekly.com
Type: eGuide
The question of productivity has become an inevitable consideration since the pandemic made home working commonplace. In this 16-page buyer's guide, Computer Weekly looks at how it's being maintained, the advantages a remote workforce brings to business and the hybrid model being embraced by workers.
-
Computer Weekly – 7 November 2023: How ExxonMobil is leading with data
By: TechTarget ComputerWeekly.com
Type: Ezine
In this week's Computer Weekly, we talk to the leader of ExxonMobil's data organisation, about the energy giant's strategy to establish enterprise-wide principles for the use of data. As the UK's Online Safety Act comes into force, we examine the tech sector's concerns over the laws around end-to-end encryption. Read the issue now.
-
Computer Weekly – 13 November 2018: Will the $34bn IBM-Red Hat mega-merger succeed?
By: TechTarget ComputerWeekly.com
Type: Ezine
In this week's Computer Weekly, after IBM buys Red Hat for $34bn to boost its cloud capabilities, we analyse how to make the deal a success. We examine the challenges that the emerging field of quantum computing presents for current encryption techniques. And our latest buyer's guide looks at storage for the internet of things. Read the issue now.
-
The great IAM - time to modernise?
By: TechTarget ComputerWeekly.com
Type: eGuide
In this e-guide, we offer a refresher in Identity and Access Management and highlight some of the trends that have an impact on it. Take a look at why IAM is a core building block for GDPR compliance and at the same time, a vital business concern. Is IAM really the way forward? And if so, is it time to modernise your strategy?
-
Cyber Security 2016 and beyond
By: TechTarget ComputerWeekly.com
Type: eGuide
Cyber risks to businesses increasingly feature in the news as a growing number of companies are targeted by attacks aimed at stealing personal and intellectual property data, but despite this coverage, studies show many companies are still ill-equipped to deal with these attacks.
-
Proactive Security: Software vulnerability management and beyond
By: TechTarget ComputerWeekly.com
Type: eGuide
In this e-guide we discover why modern security professionals are moving to a more pro-active approach to cyber defence, and how managing vulnerabilities is a key element of that.
-
The Essential Guide to MITRE Engenuity ATT&CK Evaluations
By: Palo Alto Networks
Type: eBook
In this e-book, take a comparative look at how endpoint security solutions performed in the most recent ATT&CK evaluation, and find out how Palo Alto Networks are stepping up to the challenge.
-
A Computer Weekly e-guide to SASE
By: TechTarget ComputerWeekly.com
Type: eGuide
Covid has changed everything. Yet while it has truly as introduced many new things to many spheres of activity, in terms of networking it has actually acted as an accelerant to phenomena that were just gaining momentum before the first lockdowns and stay at home orders were being made. secure access service edge (SASE) is one such case.
-
Advanced endpoint protection with TeamViewer solutions — Powered by ThreatDown
By: TeamViewer
Type: Product Overview
Protect endpoints from advanced threats with TeamViewer's Endpoint Protection solutions. Powered by ThreatDown, they provide real-time threat detection, remediation, and 24/7 managed security services. Learn more in the product overview.
-
Computer Weekly - 7 April 2020: Adapting IT to the new normal
By: TechTarget ComputerWeekly.com
Type: Ezine
In this week's Computer Weekly, we talk to four top IT leaders to find out how they are supporting their organisations through the coronavirus crisis. We look at the security best practices recommended by experts to ensure safe remote working for staff. And the CISO of Equifax explains why the firm is moving to public cloud. Read the issue now.
-
Endpoint Protection Buyer's Guide
By: CrowdStrike
Type: White Paper
Explore the critical capabilities required for modern endpoint protection, including AI-powered prevention, advanced detection and response, identity threat detection, threat intelligence, and managed threat hunting. Download the Endpoint Protection Buyer's Guide to learn how to secure your organization against today's sophisticated threats.
-
Email security: Never more important
By: TechTarget ComputerWeekly.com
Type: eGuide
In this e-guide, we look at why businesses need to address email security with a combination of awareness training and automated tools to reduce the likelihood of infection and speed up the detection of and response to email-borne threats.
-
A Holistic Approach To Security: Endpoint Protection
By: JAMF
Type: Blog
Comprehensive endpoint protection safeguards Apple, Windows, and Android devices against new and evolving threats. Learn how Jamf's defense-in-depth strategy and purpose-built solutions can secure your modern device fleet and mitigate security risks. Read the blog to discover more.
-
Focus: Securing new technology
By: TechTarget ComputerWeekly.com
Type: eGuide
The scarcity of information security professionals with the required depth and breadth of experience is one of the biggest challenges facing businesses. As businesses seek to gain competitive edge through digital transformation, they are increasingly exposing themselves to increasing risk of cyber attack.
-
How Jamf secures Apple devices
By: JAMF
Type: White Paper
Despite the strength of its built in out-of-the-box security parameter, hackers are increasingly focusing on ways of leveraging attacks against Apple devices. Download this guide to learn more and unlock key strategies you can implement to defend your Apple endpoints.
-
Blocked! Five strategies for ironclad endpoint security
By: Palo Alto Networks
Type: eBook
What can security teams do to stop attackers from penetrating endpoints and deploying ransomware or stealing information? Read this e-book to explore the top requirements to consider when pursuing a more modern approach to securing endpoints.
-
The Ultimate Guide to Cyber Hygiene
By: Tanium
Type: White Paper
It’s critical for organizations to deeply understand their risk posture and have tools in place that provide the endpoint visibility and control needed to detect and remediate security breaches. This white paper provides the benchmarks and security strategies that set IT teams up for success in proactively planning defenses against cyber threats.
-
Royal Holloway: Man proposes, fraud disposes
By: TechTarget ComputerWeekly.com
Type: Research Content
In May 2017, a strain of ransomware called WannaCry infected 32 NHS trusts in England. The NHS's report on the incident noted that all English local authorities reported being unaffected, despite also being connected to the NHS's own national network.
-
Nokia vs. 18 XDR vendors: Core benefits, features, and XDR maturity
By: NOKIA
Type: Analyst Report
This GigaOm Radar report examines 19 top XDR solutions, comparing their capabilities, emerging AI functions, and business criteria. It provides a forward-looking assessment to help decision-makers evaluate XDR offerings and make informed investments. Read the full report to learn how you can secure remote access and build user trust with XDR.
-
Nokia vs. 18 XDR vendors: Core benefits, features, and XDR maturity
By: NOKIA
Type: Analyst Report
This GigaOm Radar report examines 19 top XDR solutions, comparing their capabilities, emerging AI functions, and business criteria. It provides a forward-looking assessment to help decision-makers evaluate XDR offerings and make informed investments. Read the full report to learn how you can secure remote access and build user trust with XDR.
-
How do cybercriminals steal credit card information?
By: TechTarget ComputerWeekly.com
Type: eGuide
Cybercriminals have several methods at their disposal to hack and exploit credit card information. Learn about these, how to prevent them and what to do when hacked.
-
Managed Detection and Response: The Answer for Today's Security Needs
By: SecureWorks
Type: White Paper
Discover how Managed Detection and Response (MDR) can help address security challenges like staffing shortages, expanding attack surfaces, and lack of visibility. Learn how best-in-class MDR solutions integrate the right technology and human expertise. Read the full white paper.
-
Royal Holloway: An enhanced approach for USB security management
By: TechTarget ComputerWeekly.com
Type: Resource
USB flash drives and other USB-connected data storage devices offer a simple way of making data more portable and more easily transferrable. However, their use presents security risks that must be addressed. Apart from increasing the risk of data theft, they have often been used to transfer malware, sometimes with disastrous results.
-
The Limitations of Current Application Security Approaches
By: Contrast Security
Type: Infographic
This infographic explores the limitations of common application security approaches like WAFs and EDR solutions. It highlights their lack of visibility into application-level threats and the need for more robust application security. Read the full infographic to learn how you can better protect your applications.
-
The Limitations of Current Application Security Approaches
By: Contrast Security
Type: Infographic
This infographic explores the limitations of common application security approaches like WAFs and EDR solutions. It highlights their lack of visibility into application-level threats and the need for more robust application security. Read the full infographic to learn how you can better protect your applications.
-
ThreatDown Endpoint Protection onepage
By: TeamViewer
Type: Product Overview
Protect your endpoints with advanced malware protection that combines predictive threat detection, proactive blocking, and integrated remote access. Learn how ThreatDown Endpoint Protection can safeguard your organization against zero-day threats. Read the full product overview.
-
Active defence through deceptive IPS
By: TechTarget ComputerWeekly.com
Type: Research Content
This article in our Royal Holloway security series explains how intrusion prevention systems (IPS) can be used with a 'honeynet' to gather intelligence on cyber attacks
-
The difficulties of defending against web tracking
By: TechTarget ComputerWeekly.com
Type: Research Content
This article in our Royal Holloway information security series introduces you to web tracking, provides an overview of how organisations track users and discusses a few of the difficulties you may face when trying to defend against tracking.
-
Gartner's 2024 Hype Cycle for Endpoint & Workspace Security Insights
By: Tanium
Type: Gartner Research Report
The rapidly evolving cybersecurity landscape demands innovative solutions – and innovation is abundant. Read The Hype Cycle™ for Endpoint and Workspace Security to distinguish between transient trends and real advancements in the endpoint and workspace security arena.
-
Aircall trusts JAMF to manage and secure its Macs
By: JAMF
Type: Blog
Aircall is a cloud-based call center and phone system solution for companies. With devices, specifically macs, playing a crucial role in the worker’s day-to-day operations, endpoint security was a critical necessity. With JAMF, Aircall is able to manage and secure their array of macs, preventing key threats. Read on to learn more.
-
SAP and Jamf enterprise mobility case study
By: JAMF
Type: Case Study
SAP is now the market leader in enterprise application software, with 77% of the world’s transaction revenue touching an SAP system. SAP recently Migrated 84,000 iOS devices from their previous MDM to Jamf Pro. Access this case study to learn what security benefits led SAP to make this decision.