Iam: Globalization & Large-Scale Enterprise
By: IC Consult View more from IC Consult >>
Download this next:
IAM: ServiceNow + AlertEnterprise partnership
By: ServiceNow and Alert Enterprise
Type: Video
Thanks to their relationship with ServiceNow, AlertEnterprise’s workforce identity and access management solutions are more efficient, effective – and secure.
Discover the impact of the partnership and its integrations with AlertEnterprise Guardian in this series of videos.
These are also closely related to: "Iam: Globalization & Large-Scale Enterprise"
-
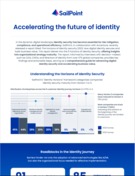
How digital identity secures and fuels business value
By: SailPoint Technologies
Type: Infographic
According to a recent study, 66% of organizations believe underdeveloped asset and data management capabilities present the greatest obstacle in the journey to identity maturity.
This infographic explores the state of identity security maturity, analyzing which sectors and organizations are seeing the most success, as well as how key trends are shaping the future of the market.
Download now to learn more.
-
Managing the risk of third-party identities
By: SailPoint Technologies
Type: Analyst Report
The efficiency demanded by modern business has led organizations to enlist more third-party workers than ever before. While these service providers are effective, the access they require to critical infrastructure necessitates additional identities, leading to further risk.
Effectively managing these identities and regulating access presents a complex challenge, requiring an all-encompassing solution to bring these crucial non-employee identities under control.
This KuppingerCole Executive View looks at some of the options available for managing non-employee and other third-party identities, including a technical review of SailPoint’s Non-Employee Risk Management solution.
Read on to learn more.
Find more content like what you just read:
-
How to manage an endless stream of digital identities
By: SailPoint Technologies
Type: White Paper
The quantity of identities that most organizations are responsible for is so overdeveloped, that for many, manual identity management is no longer possible.SailPoint has developed their own AI-driven identity security solution, designed to affectively mitigate the risks presented by unmanaged identities. Download now to learn more.
-
What to look for in an IAM solution
By: SailPoint Technologies
Type: White Paper
In a market filled to the brim with solutions, how do you know which access management solution is right for your organization? This white paper provides checklists for evaluating solutions, including sets of qualifying questions which can be used to evaluate solutions across a set of criteria required. Read on to learn more.
-
Autonomous identity security: Combining IGA and automation
By: SailPoint Technologies
Type: White Paper
Managing identities was simpler when you only had to worry about user profiles, but What if machine identities could manage themselves, without presenting a risk for security? Autonomous identity security combines automation with IGA practices to create a system that manages access without the need for human input. Read on to learn more.
-
Identity security with the power of AI
By: SailPoint Technologies
Type: eBook
Today’s enterprises are each responsible for up to millions of identities. But the scope of identity management means it is no longer feasible for humans to manage and secure these identities. SailPoint Identity Security for Cloud is designed to overcome these challenges by using AI to keep track of identities. Read on to learn more.
-
Role management with AI & ML: Economic benefits
By: SailPoint Technologies
Type: Product Overview
In this day and age, role management is complex and labor intensive, making it difficult for organizations to fully realize savings without eclipsing them with costs.This data sheet looks at How SailPoint tools incorporate AI and ML to automate role management, allowing you to achieve the benefits, unburdened by excess costs. Read on to learn more.
-
Gain visibility with automated identity management
By: SailPoint Technologies
Type: Product Overview
Visibility is at the heart of identity management today, but with limited resources and manpower, most organizations aren’t able to maintain it. Download this data sheet to learn how SailPoint uses AI and ML to automate tasks and maintain visibility across your organizations’ identity surfaces, keeping a direct line of sight and staying secure.
-
Free up IT resources with SailPoint Identity Security
By: SailPoint Technologies
Type: Video
Business IT is both a marathon and a sprint. SailPoint Identity Security uses automation to streamline operations, allowing your IT team to reallocate its resources to focus on higher value initiatives. Watch this video now to learn more about the benefits of SailPoint identity security.
-
Data access findings: 305 experts surveyed
By: SailPoint Technologies
Type: Analyst Report
Managing access has always been a challenge, but with cloud adoption as well as the advent of remote work, organized data access is more elusive than ever before. Download this report to learn more about the state of data and identity access governance and unlock key findings.
-
Managing third-party identity risk
By: SailPoint Technologies
Type: Data Sheet
Today’s organizations no longer reside behind a digital perimeter, with countless other third-party entities presenting access risk. SailPoint Non-Employee Risk Management aims to bolster identity security by extending advanced governance controls to large and complex populations of non-employee users. Download this data sheet to learn more.
-
Managing the third-party risk of non-employee identities
By: SailPoint Technologies
Type: White Paper
Organizations utilize non-employee workers and services to supplement their workforce, but each of these non-employee entities presents an increase in third-party risk. This white paper explores how non-employee identities present new demands to organizations’ existing authentication systems and protocols. Read on to learn more.
-
Secure identities with AI & ML
By: SailPoint Technologies
Type: Product Overview
Enterprises today hold millions of individual identities, each presenting a security risk that must be managed. With AI and ML at the core, SailPoint Identity Security Cloud is architected to allow enterprises to manage access across the most complex cloud environments. Read on to learn more.
-
SailPoint, IBM, Oracle, and more: Comparing IGA vendors
By: SailPoint Technologies
Type: Analyst Report
Traditionally, identity governance administration (IGA) was called the passive side of governance, where organizations would implement largely on premises to improve their regulatory compliance positions. This report provides an overview of the current IGA solution market, highlighting and comparing the leading vendors. Read on to learn more.
-
Secure Access for the Identities Driving Your Key Initiatives
By: CyberArk
Type: White Paper
With 99% of IT security decision-makers reporting they expect to face an identity-related compromise in the year ahead, it’s important to understand why.This white paper investigates how you can develop an effective access security program so that you can defend your organization from compromised identities. Read on to learn more.
-
Secure Identities with the Power of Modern MFA
By: CyberArk
Type: eBook
“The only constant in life is change.” Today, enterprises around the world are caught in the middle of a major transformation. As a result of this digital transformation there has been an uncontrollable surge of identities, making identity security the top priority for security leaders. Download this e-book to learn more.
-
Building a Multi-layered Approach to Securing Access
By: CyberArk
Type: White Paper
According to a study conducted by CyberArk, 99% of IT security decision-makers agree they’ll face an identity-related compromise in the year ahead. If an attack is inevitable, how can you reduce risk by preventing breaches and neutralizing attackers who’ve broken in? Download to learn how.
-
Identity and Access Management is Leading the Way for Identity Security
By: CyberArk
Type: ESG Research Report
Recent findings show 80% of IT professionals expect the total number of identities under management to increase by more than double. This report, produced by TechTarget’s Enterprise Strategy Group (ESG) synthesizes the findings from recent research to provide a holistic view of the IAM landscape. Download now to learn more.
-
Critical Gaps in Securing Identities
By: CyberArk
Type: White Paper
Enterprises today rely on hundreds of applications to achieve their business and operational goals. In this report, Media Group EU Information Security Executive News Editor, Tony Morbin, takes you through the key findings from a recent study conducted with the help of 214 senior cybersecurity professionals. Read on to learn more.
-
Third-party Leadership Report 2023: Access Management
By: CyberArk
Type: Analyst Report
With identities now the center of security concerns, access management is more important than ever before. This report provides an overview of the access management product market, presenting you with a compass to help you to find the product or service that best meets your organization’s needs. Read on to learn more.
-
Research analysis: Steps to stronger identity security in 2024
By: SailPoint Technologies
Type: Webcast
Tune into this webinar to walkthrough a detailed analysis of the identity security space with a panel of experts, which includes 9 identity security maturity barriers (including budgets and technical debt), the industry landscape, and 6 steps to stronger identity security.
-
Horizons of identity security
By: SailPoint Technologies
Type: Research Content
Securing an identity means securing everything that that identity has access to, and as digital evolution continues, so too must IAM security. This report attempts to forecast the future of identity and access security, focusing on its rapid growth and potential to eclipse other important aspects of the modern enterprise. Read on to learn more.
-
The guide to securing digital identities and minimizing risk
By: SailPoint Technologies
Type: eBook
Ransomware, phishing, credential stuffing, and supply chain attacks all attacks involve gaining a foothold in a network, often through a compromised identity; and while there are other avenues of attack, identity is in many ways the master key. Download this e-book to gain access to a guide to develop a stronger identity security platform.
-
Best practices for ensuring security of all identities
By: SailPoint Technologies
Type: eBook
Compromised identities are an ever-present danger and are often found used by hackers as the entry point for calculated attacks. This book explores how strong identity security helps mitigate identity-related risk from hackers and human error, as well as how it can be used to streamline fortify governance and compliance. Download now to learn more.
-
Security leader’s guide to identity security
By: SailPoint Technologies
Type: eBook
Providing fast, accurate access to digital resources for those who need it is essential for organizations to secure business and gain a competitive edge. This e-book will review the fundamentals of identity security and discuss how identity security best protects critical assets. Read on to learn more.
-
Mapping out your IAM strategy in Atlassian Cloud
By: Atlassian
Type: eBook
Discover in this e-book how you can extend your company-wide IAM policies and build a proactive defense strategy to protect your users and data in Atlassian Cloud.
-
Smashing PAMkins: A Developer's Nightmare Before Christmas
By: CyberArk
Type: Webcast
Privileged access management (PAM) is complex, with IT teams and developers forced to navigate the security risks associated with privileged access. This webcast looks at privileged access and the challenges it presents for developers. Tune in now to learn more.