This resource is no longer available
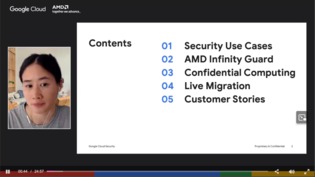
In an evolving threat landscape, how can you protect your sensitive data in the cloud while staying compliant with data protection regulations?
In this webcast, you’ll learn about the confidential computing model: a new security paradigm that uses hardware-based memory encryption to keep data and code protected when being processed. In this model, the cloud service provider and the guest VM are isolated from each other – so neither has access to the resources of the other.
Tune in now to find out how you can prevent instances of unauthorized access and safeguard your sensitive cloud data.